Whatsapp is
the most popular Messaging platform that is used by billions of people
across the world. Whatsapp has become very popular because of its
attractive and striking features like cross-platform messaging service,
Online media sharing, Free Messaging service, voice calling
etc. Most of the smart phone users like for iPhone, BlackBerry,
Android, Windows Phone and Nokia are fascinated towards whatsapp
messenger as it provide innovative and amazing features.
People can share their views, images and many more using their own
Whatsapp account. It would be more fun by hacking your friend’s account.
Accessing the account of some other people like friends, relatives and
beloved ones always sounds interesting. It may not be for bad reason,
but sometimes you like to view other’s account. People have many queries
regarding How to Hack Whatsapp account? Here, you can find simple steps
for hacking some other’s account. Follow these easy steps and HACK
WhatsApp account. ENJOY!!!
If you want to access the whatsapp account of your friend, you need to find the MAC address of their account. Follow the below steps in order to hack your friend’s account.
Step 1: Uninstall Whatsapp Account from your device



Device : Spoofing App
iPhone (or) other device : MacDaddy X or WifiSpoof.
–>Use this app to change your MAC address.
Android : BusyBox, Terminal Emulator
–>Both these apps are available for free on Google Play.
Assume we’ll use the eth0 interface. In the terminal emulator, enter “ip link set eth0 address XX:XX:XX:XX:XX:XX” and “ip link set eth0 broadcast XX:XX:XX:XX:XX:XX”, where eth0 is the interface you identified and XX:XX:XX:XX:XX:XX is your target’s MAC address. In order to verify that you’ve changed your MAC address successfully, enter “ip link show eth0.”
Step 7: Re-Install and configure whatsapp account on your Device


Techniques to Hack Whatsapp Account
Whatsapp account of your friends or some others can be hacked by following few methods. There are mainly two methods of accessing other’s whatsapp account. We are giving you detailed information regarding the techniques for hacking or accessing one’s whatsapp account. Follow these simple steps and enjoy hacking your friends’ whatsapp account.Technique 1: MAC Spoofing
A Media Access Control address (MAC address) is a 12-character unique identifier assigned to the network adapter of your WiFi device. A MAC address can be used to uniquely identify the smart phone of your friend whom you want to hack the Whatsapp account on the Internet or the local network.If you want to access the whatsapp account of your friend, you need to find the MAC address of their account. Follow the below steps in order to hack your friend’s account.
Step 1: Uninstall Whatsapp Account from your device

- Initially, you must uninstall your Whatsapp account from your device.
- Don’t worry! Your account can be reinstalled and configured at the end of your Hacking process.
- Be Careful! Make sure that your Whatsapp account on your mobile device is completely uninstalled successfully.
- Get the mobile phone of the victim that you desire to access. Though it is little bit rugged, try to acquire the mobile phone of the victim.
- The victim’s mobile phone will be essential at two variant steps throughout the hacking process.
- Be cautious while using the victim’s phone. Don’t take much time and try to place it back before the victim starts to locate the device.

- A MAC address is a 12-character unique identifier assigned to the mobile device which can be served as its online identity.
- A MAC address varies from one device to other. So, find the platform of the smart phone that is used by the victim.
- A MAC address consists of six pairs of digits that are separated by colons. For Example, it looks like (01:53:35:47:78: cb).
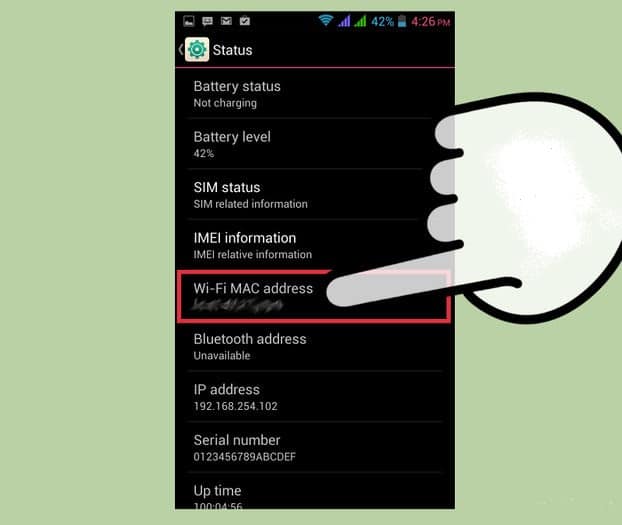
Smartphone Platform: How to find MAC Address?
Android : Settings >> About Phone >> Status >> Wi- Fi MAC address
iPhone : Settings >> General >> About >> Wi-Fi Address.
Windows Phone : Settings >> About >> More info >> MAC Address.
BlackBerry : Options >> Device >> Device and Status Info >> WLAN MAC

- Get the MAC address of your Mobile device and save and ensure that you store it in a secure manner.
- Again, you’ll require your MAC address to use your mobile device after completion of your hacking process.
- Spoofing the MAC address allows your mobile device look similar as victim’s device.
- By spoofing there is an advantage of letting you to persuade Whatsapp that you are logging into your own account.
- But, truly you are trying to log in into the victim’s Whatsapp account.
Device : Spoofing App
–>Use this app to change your MAC address.
Android : BusyBox, Terminal Emulator
–>Both these apps are available for free on Google Play.
- In the terminal, type “ip link show” and you can view a list of interfaces.
- Identify the one that has your MAC address.
Assume we’ll use the eth0 interface. In the terminal emulator, enter “ip link set eth0 address XX:XX:XX:XX:XX:XX” and “ip link set eth0 broadcast XX:XX:XX:XX:XX:XX”, where eth0 is the interface you identified and XX:XX:XX:XX:XX:XX is your target’s MAC address. In order to verify that you’ve changed your MAC address successfully, enter “ip link show eth0.”
Step 7: Re-Install and configure whatsapp account on your Device

- After installing and configuring Whatsapp account on your device, you access the victim’s whatsapp account.
- Enter the victim’s phone number so as to set up WhatsApp rather than your own.
- This allows you to receive and send messages from the victim’s account.

- During the WhatsApp configuration process, confirmation code will be sent to the victim’s phone number.
- Access the victim’s phone for the last time to acquire that verification code.
- Enter it into WhatsApp that is on your phone.
- Finally, you have successfully hacked the Whatsapp account of your target.
- If you don’t wish the victim to detect about your spoofing, make sure to delete the confirmation code from their device.

- Similarly, repeat the instructions to change the MAC address, but you need to change it to your original address rather than the victim’s MAC address.
- Now, your mobile will be restored to its original position and ensures that there are no future problems with Internet usage or connectivity issues.