Google's engineers love to hide some pretty cool tricks at the most
unexpected places. Add to that Google's policy of giving 20% of working
time to its engineers to do what they want, and you have a search engine
filled with lots of entertaining Easter eggs and tricks.
Sadly, most of these tricks are still a secret, but every now and then,
Google employees leak these cool insider pranks and the whole world gets
to know about them. Here, I have created a list of all such known
Google tricks and Easter eggs that are still "working."
Kerning
Kerning means adjusting the spacing between characters. So, how would
you expect Google to describe it? Literally, off course. When you
search Google for Kerning, the spacing of the word Kerning is changed as
compared to that of other words. This only works with personalized
results disabled.
Conway's Game Of Life
Conway's Game Of Life is a game that indicates how cellular life evolves
based on the initial configuration. If you search Google for Conway's
Game of Life, you will get a results page with the game running in the
background.
Jason Isaacs
Just search for Jason Isaacs and Google will return a page saying Hello
to him. This only works on Google UK. This is a reference to Kermode and
Mayo's Film reviews which greets Jason with hello every week.
Bacon Number {Actor Name}
Kevin Bacon is a famous hollywood actor who was quoted as saying that he
has worked with everybody in hollywood or somebody who has worked with
them in 1994. This led to many websites being launched about his claim
in 2007. Bacon seeing this immense response launched a charitable
website called Six Degrees, which is based on a theory that everyone in
hollywood has worked with Kevin Bacon through a chain of six
acquaintances or less. An actor gets as many degrees as he is distant
from Kevin Bacon's movies in terms of people in the chain of
acquaintances.
Google too has now involved Six Degrees of Bacon in its search results.
For example, searching Google for Bacon Number Johnny Depp gives Depp's
Bacon number to be 2.
Google knows how to celebrate the holidays
Searching Google for a holiday will make Google return a page decorated
with items representing that holiday. For example, searching Google for
Christmas returns a page decorated with Christmas lights. This also
works for Kwanzaa, Hanukkah, Halloween and Festivus. These Easter Eggs
based on a festival are only activated when that festival is near.
Zerg Rush
Search Google for Zerg Rush and you will see the O's of Google
attacking the search results page. They will attacking every result one
by one. There is a health bar which indicates how injured a search
result is. You can also kill these O's by clicking on them. They also
have health bars which indicates their health. You get points on the
basis of how many O's you kill. The aim of this game is to beat as many
O's as possible.
Askew or
Tilt
Ever had the chance of searching Google for
Askew or
Tilt?
If you have, then you already know what comes up. If you haven't, do it
now and you will see the search results page literally tilt to give you
a better idea of what these words mean. This will work only if you use
latest browsers which support HTML5 and CSS3. So, Internet Explorer
users, use Firefox, Google Chrome or Safari for a while to use this.
Do a barrel roll
'Do
a barrel roll' in its true sense means to do a 360 degree spin. Google
takes practical demonstrations way too seriously for this one and
literally spins the search results page to give you a clearer idea of
the meaning of this phrase. Don't believe me? Go
search Google for
Do a barrel roll now and see your world turn around.
This Easter egg is apparently a tribute to Star Fox, a video game series developed by Nintendo, because searching Google for
Z or R Twice also does the barrel roll, just like in Star Fox. Many
bloggers
interpreted a lot of different things from this, but Google clarified
that this fun trick was created by a Google Engineer solely for the
purpose of entertaining users along with showing the power of new HTML5
and CSS3 technologies. Like the previous Easter egg, this will only work
in modern browsers.
Binary, Octal and Hexadecimal Number systems
Another one of those literal Google Easter eggs. If you search Google for
"Binary",
"Octal" or
"Hexadecimal"
(without quotes) with Search Plus Your World disabled, Google will show
the number of results in the same number system. For example, searching
Google for hexadecimal will return the number of results like in the
image below.
Recursion
The "Did you mean?" feature of Google often helps many users to get to
the right results when they type something different from what they
intended to search. If you search Google for recursion, the same feature
takes you to an endless loop of clicks all linking to the same results
page thereby completing recursion, which occurs when something calls
itself. Seriously geeky.
Anagram
Another one of those "Did you mean?" Easter eggs. Search Google for
Anagram and Google will instantly ask whether you meant "Nag A Ram"
which is one of the anagrams of the word "anagram." Google really shows
their word-playing skills with this one.
Asking Google to
define Anagram makes Google ask if you meant
nerd fame again.
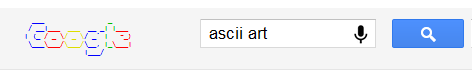
ASCII Art
Are you a fan of ASCII art? Google surely is. Search Google for
ASCII art
and Google will greet you with a search results page having an ASCII
version of the Google logo at the place where normal logo should have
been. This Easter egg does not work anymore. When it did work, it looked
like the image given below.
Google Calculator Easter Eggs: The loneliest number
Do
you know which is the loneliest number? Ask Google Calculator. Search
Google for the loneliest number and the in-search Google Calculator will
give one as the answer, which apparently is a tribute to the Harry
Nilsson's song "One."
Once in a Blue Moon
Ever
wondered how much is 'once in a blue moon'? You must have heard this
phrase often but Google calculator will give you the exact value of this
phrase and surprisingly, it denotes frequency rather than time. Go
search Google for this to get "1.16699016 × 10-8 hertz" as the answer.
The number of horns on a unicorn
Want to know the number of horns on a unicorn? Google calculator can help. Searching Google for
the number of horns on a unicorn will give 1 as the answer.
Answer to the Ultimate Question of Life, the universe and everything
Google
is omniscient. Even the "answer to the ultimate question of life, the
universe and everything" is known to Google. Just search Google for the
above phrase and Google calculator will give you an answer. What are you
waiting for? Just go to Google and find the true meaning of life.
[Pause to give you the time to search]
Surprised by the answer (42)? This is a reference to The Hitchhiker's
Guide to the Galaxy, a popular novel based on a radio show (by the same
name) of the late seventies. Google engineers surprised you with these
tricks, didn't they?